Cost / License
- Free
- Open Source
Application types
Platforms
- Linux
- Tor Browser
- GNOME
- Tor
- Thunderbird


OpenVPN Connect provides flexible VPN solutions to secure your data communications, whether it's for Internet privacy, remote access for employees, securing IoT, or for networking Cloud data centers.




BitTorrent site for downloading movies, music, software via torrents. Offers magnet links, peer-to-peer sharing, and user ratings.

1337x is a website that provides a directory of torrent files and magnet links used for peer-to-peer file sharing through the BitTorrent protocol. According to the TorrentFreak news blog, 1337x is the third most popular torrent website as of 2021.
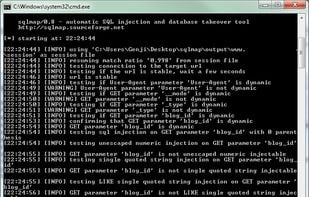
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range...
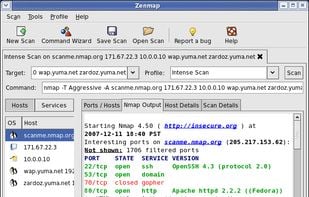
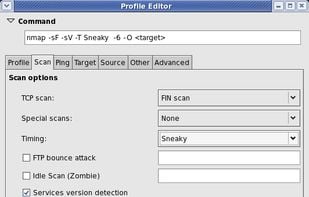
Free, open-source utility for network security auditing and exploration with capabilities for OS detection, service identification, and large network scans.
WikiLeaks specializes in the analysis and publication of large datasets of censored or otherwise restricted official materials.
Deluge is a full-featured BitTorrent client for Linux, Unix and Windows. It is written in python, uses ![]() libtorrent (rasterbar) at its core and GTK for the main user interface along with web and console interfaces for advanced client/server...
libtorrent (rasterbar) at its core and GTK for the main user interface along with web and console interfaces for advanced client/server...
Desktop client for large-scale torrent downloads, offering simultaneous downloads, bandwidth optimization, and scheduling. Supports RSS downloads.
The Social-Engineer Toolkit is an open source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly.

John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix systems, supported...
Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system.
GNU Wget is a free software package for retrieving files using HTTP(S) and FTP, the most widely-used Internet protocols. It is a non-interactive command line tool, so it may easily be called from scripts, cron jobs, terminals without X-Windows support, etc.
A low-cost, capable little PC which can be used for many of the things that your desktop PC does, like games, spreadsheets and word-processing. It also plays high-definition video. We want to see it being used by children and young people all over the world to learn programming.


Offers Git-based code hosting, integrated issue tracking, a project wiki, pull requests, and collaboration tools with support for private or public repositories.
Web-based Git hosting service facilitating collaboration, with features like issue tracking, social networking, and wikis for project management.

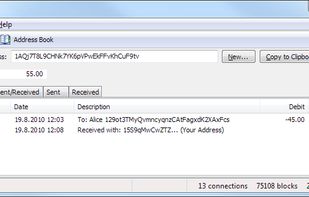
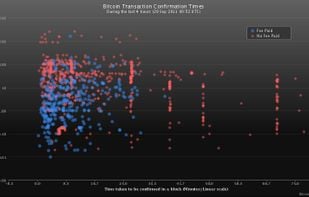
Bitcoin is a peer-to-peer digital currency. Peer-to-peer (P2P) means that there is no central authority to issue new money or keep track of transactions. Instead, these tasks are managed collectively by the nodes of the network.

WiGLE (or Wireless Geographic Logging Engine) is a website for collecting information about the different wireless hotspots around the world.
With the power of the Wayback Machine, you can go back in time to see how a website has changed and evolved through the history of the Web.
OpenSSH is a free version of the SSH connectivity tools that technical users rely on. OpenSSH encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other attacks.
Hyper™ is a beautiful and extensible, cross-platform terminal built on open web standards. It provides an elegant command-line experience that is consistent across all supported platforms which includes macOS, Windows and various Linux distributions like Fedora and Debian.
Secure, cost-effective remote access and support for your computer, from your desktop or mobile device.

WifiKill is an Android app that was first introduced in 2011 by developer "bponury". The app was designed to allow users to monitor and control their WiFi networks, enabling them to see which devices were connected and to disconnect any unwanted devices.
Searx is a free internet metasearch engine which aggregates results from more than 70 search services. Users are neither tracked nor profiled. Additionally, searx can be used over Tor for online anonymity.



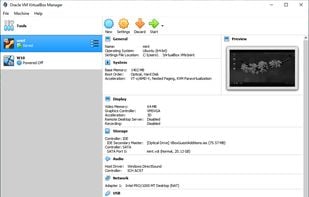
Open source virtualization tool supporting x86/AMD64, runs on Windows, Linux, Mac, Solaris. Offers portable, lightweight, ad-free use.
Open-source FTP client supporting FTP, FTPS, and SFTP with features like large file transfers, site management, and cross-platform because of FileZilla Server.
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing, originally forked from Backtrack Linux by the Offensive Security team.

Arch Linux is an independently developed, x86_64 optimized GNU/Linux distribution targeted at competent Linux users. It uses pacman, its home-grown package manager, to provide updates to the latest software applications with full dependency tracking.

The Linux kernel is the core component of the Linux operating system. It's responsible for managing the system's resources and facilitating communication between hardware and software. It was first created by Linus Torvalds in 1991 and is open-source, allowing for...
Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners such as Nexpose - for free. This helps prioritize remediation and eliminate false positives, providing true...
Network scanner discovers devices, monitors ISP performance, sets security checks. Use advanced tools to analyze settings and find hidden cameras.
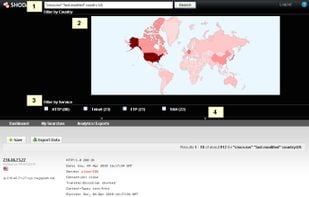
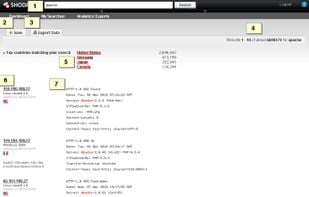
Shodan is a search engine that lets you find specific computers (routers, servers, etc.) using a variety of filters. Some have also described it as a public port scan directory or a search engine of banners.
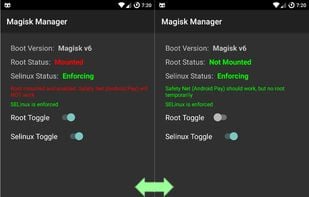
Installing Magisk will give you ROOT, a super powerful Systemless Interface, Magisk Modules support, and hide from tons of integrity tests like SafetyNet!.
App Cloner is a specialized tool that lets you create and install copies of your existing Android apps so you can do things like utilize multiple logins at various apps such as Facebook and Skype.


Facilitates device communication, enabling notifications, SMS replies, file sharing, and remote control across multiple operating systems.
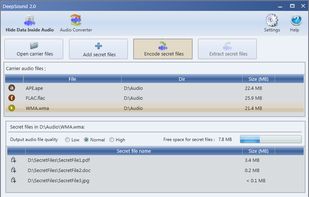
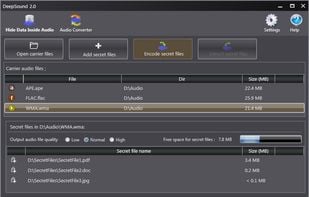
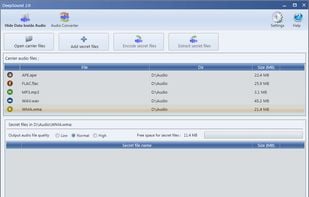
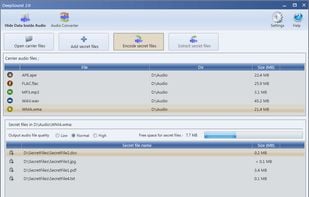
DeepSound is a steganography tool and audio converter that hides secret data into audio files. The application also enables you to extract secret files directly from audio files or audio CD tracks.
Vim ("Vi IMproved") is an advanced text editor that allows syntax highlighting, word completion and has a huge amount of contributed content. It also has a GUI version called GVim.
Guerrilla Mail gives you a disposable email address. You can give your email address to whomever you don't trust. You can read the email using Guerrilla Mail, click on any confirmation link, and even reply.
Secure Swiss-based email with end-to-end encryption and zero third-party access. Available across devices, offering a free version to promote privacy.

Firefox Developer Edition brings you latest features, fast performance, and the development tools you need to build for the open web. Its powerful development tools will extend your ability to work across multiple platforms from one place.

Privacy-focused search engine offering Zero-click Info, instant answers, and more, built from open-source software for a user-friendly experience.

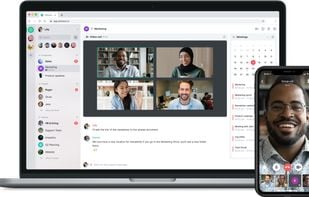
A secure collaboration app with end-to-end encryption and interoperability across web, desktop, and mobile. Includes chat, voice, and video calls.
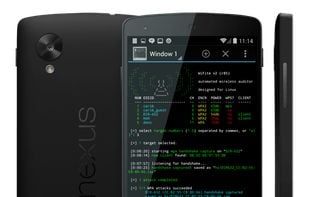
The Kali Linux NetHunter project is the first Open Source Android penetration testing platform for Nexus devices, created as a joint effort between the Kali community member “BinkyBear” and Offensive Security. NetHunter supports Wireless 802.

An encrypted messaging app focused on privacy, supporting texts, calls, photos, videos, files, and group chats, with no ads or trackers.
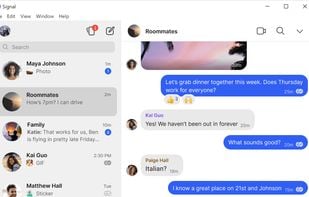
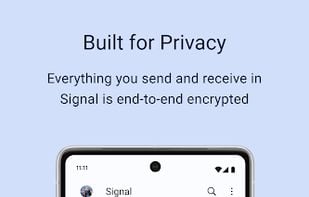
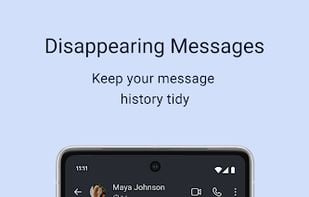
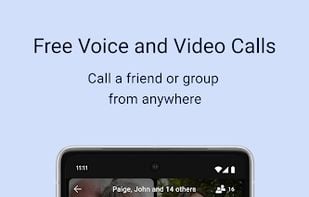
Enhance privacy with a secure, portable browser that hides your IP and encrypts connections on multiple platforms, maintaining anonymity.
Comments
Owncloud, nextcloud - to save and edit documents on server ZeroNet - P2Pchat / forums / social network [Edited by mcl12345, May 06]
Great list. Thanks for compiling.
I always enjoy seeing software I wasn't already familiar with;
In addition to the many programs you listed: I also find the following very useful at times: Popcorn Time - great for movies.. (all movies, especially new releases). Truecrypt/Veracrypt - excellent file/drive encryption tools. Lastpass - password management. Private Internet Access - best paid - VPN. KeyScrambler - anti keylogger. Bitnami - pre-built virtual machine platforms.
uTorrent isn't good for privacy since it's closed source and propriatery, use qBittorrent, Deluge or Transmission (Tribler is also good but it's experimental)
you shouldn't be using uTorrent anyway its basically a virus. it can download programs without asking and they've also distributed adware and bitcoin miners in the past lol
Agree with OR3O, µTorrent is a terribly dodgy piece of software. qBittorrent is the closest interface. Deluge and Transmission are ported from Linux (I know Transmission was), they're both good.
spectrumsss, is Tribler still in beta? It's been that way for years. I honestly didn't know it was still developed...
It's out of beta, however on their website, they claim "Our anonymity is not yet mature" and it doesn't seem like that will change soon. I wouldn't really recommend it if you're downloading something illegal. If you must use it, use it either with a Tails OS live ISO or with a Whonix virtual machine.
It's out of beta, however on their website, they claim "Our anonymity is not yet mature" and it doesn't seem like that will change soon. I wouldn't really recommend it if you're downloading something illegal. If you must use it, use it either with a Tails OS live ISO or with a Whonix virtual machine.
It's out of beta, however on their website, they claim "Our anonymity is not yet mature" and it doesn't seem like that will change soon. I wouldn't really recommend it if you're downloading something illegal. If you must use it, use it either with a Tails OS live ISO or with a Whonix virtual machine.