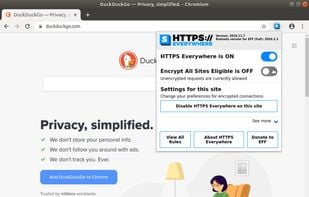
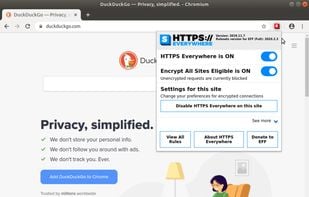
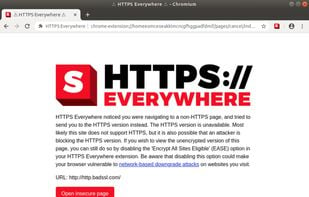
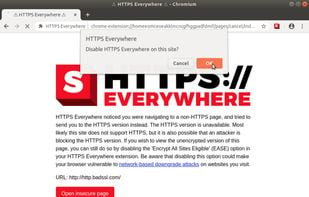
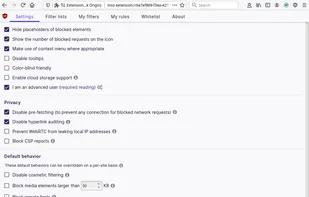
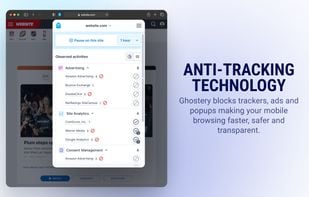
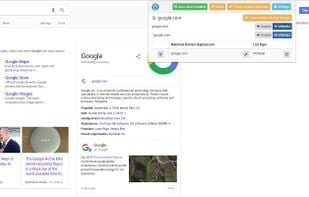
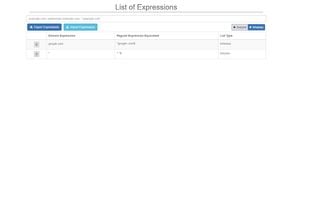
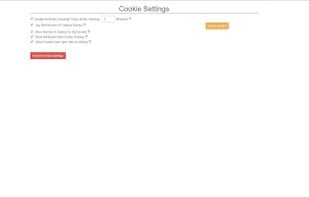
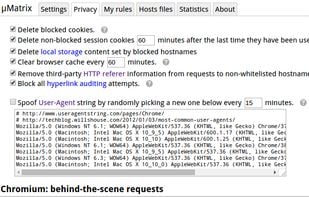
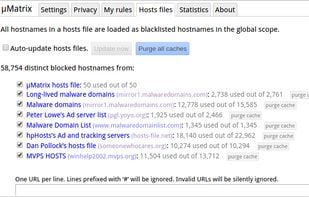
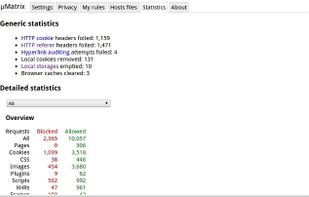
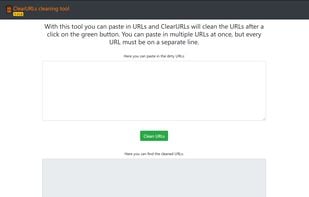
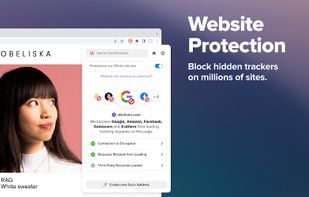
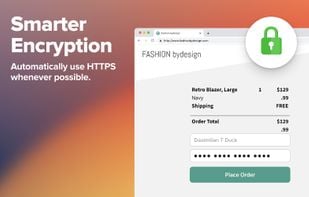
HTTPS Everywhere is a browser extension produced as a collaboration between The Tor Project and the Electronic Frontier Foundation. It encrypts your communications with a number of major websites.
Cost / License
- Free
- Open Source
Application type
Platforms
- Online
- Vivaldi Browser
- Google Chrome
- Yandex.Browser
- Opera
- Chromium
- Firefox