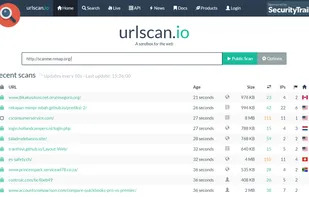
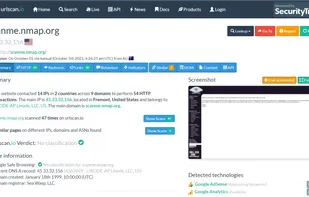
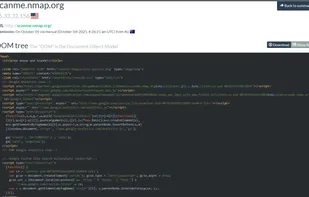
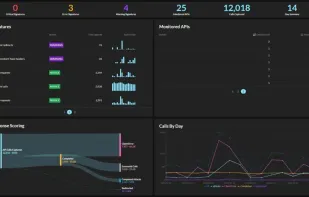
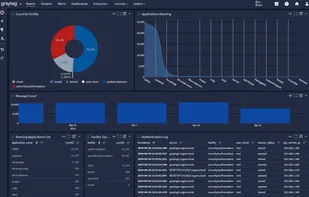
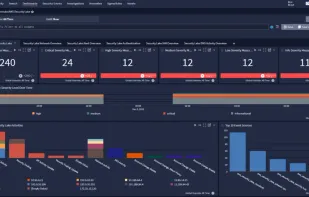
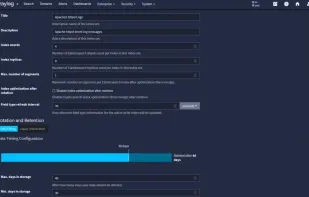
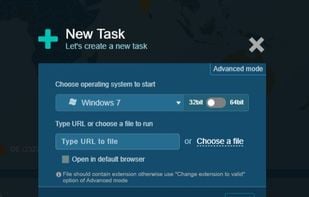
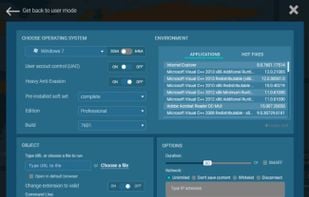
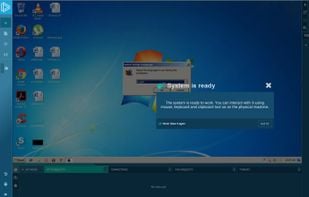
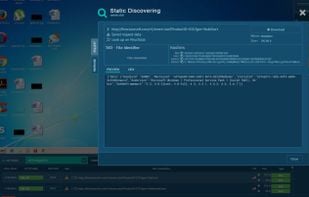
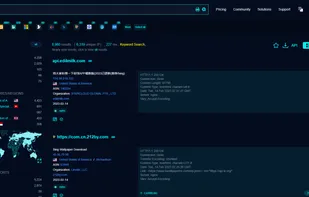
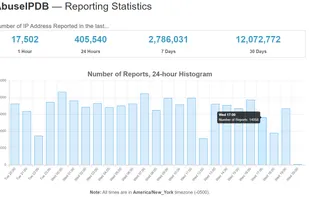
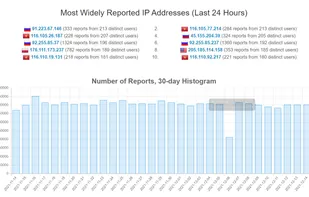
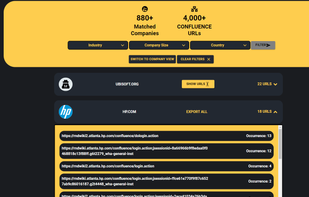
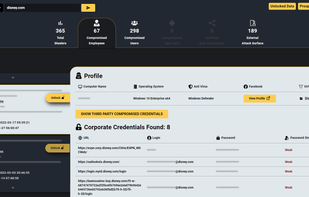
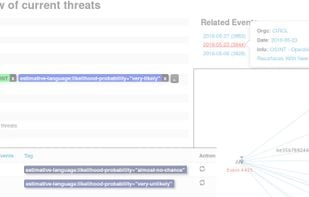
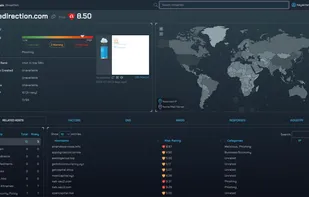
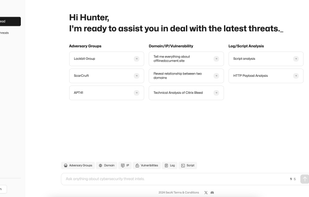
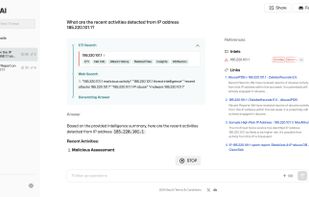
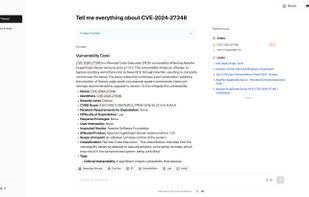
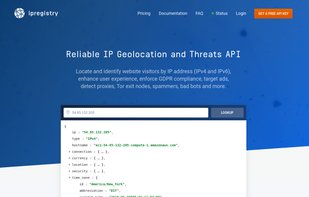
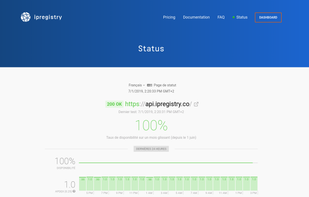
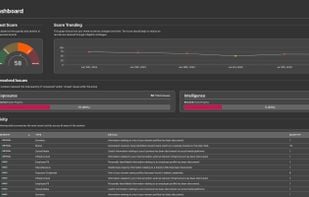
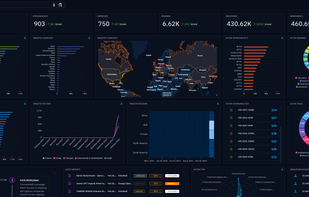
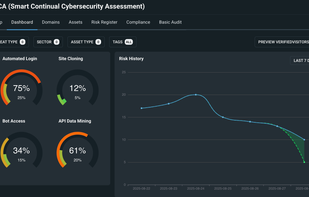
Inspects files, domains, IPs, and URLs with 70+ scanners, sharing results with the security community. Free for end-users for non-commercial use.
Cost / License
- Free Personal
- Proprietary
Application types
Platforms
- Mac
- Windows
- Linux
- Online
- Microsoft Edge
- Google Chrome
- Software as a Service (SaaS)
- Mozilla Firefox