Phantom is described as 'The Phantom protocol is a system for decentralized anonymization of generic network traffic. It has been designed with the following main goals in mind:' and is a anonymizing network in the network & admin category. There are more than 10 alternatives to Phantom for a variety of platforms, including Linux, Mac, Windows, BSD and Android apps. The best Phantom alternative is Tor, which is both free and Open Source. Other great apps like Phantom are I2P, Hyphanet, Nym and GNUnet.




Lantern allows you to give or get access to the internet through other users around the world connected by a trust-based peer-to-peer network.
dn42 is a big dynamic VPN, which employs Internet technologies (BGP, whois database, DNS, etc). Participants connect to each other using network tunnels (GRE, OpenVPN, Tinc, IPsec) and exchange routes thanks to the Border Gateway Protocol.
SMesh is a seamless wireless mesh network being developed by the Distributed System and Networks Lab at Johns Hopkins University.
Ninux is an Italian wireless network community with the goal of creating and expanding a free, open and experimental computer network. It uses the OLSR (Optimized Link State Routing) Protocol, an IP routing protocol optimized for mobile ad hoc networks.
Digitatas is a digital tree, a sapling to give technology to children of the Digital Generation. Under Open Hardware licensing by Open_Sailing and openet.org.
Babel is a loop-avoiding distance-vector routing protocol for IPv6 and IPv4 with fast convergence properties. It is based on the ideas in DSDV, AODV and Cisco's EIGRP, but is designed to work well not only in wired networks but also in wireless mesh networks, and has been...
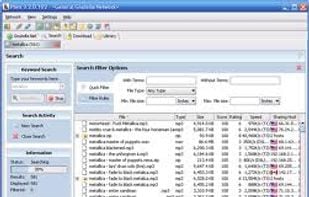
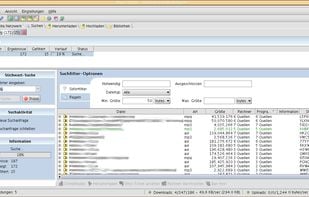
Phex is a peer-to-peer file sharing client for the Gnutella network. It is free software and without spyware or adware. Phex is released under the GNU General Public License. Phex is based on Java technology and therefore available for many different systems that offer a Java 1.
Main Features: All in one application: TOR, VPN and Proxy; Hide your IP address; Bypass Internet censorship and filtering; Hide your online activities from your ISP; Access blocked websites; Access Geo-restricted web contents (e.g.