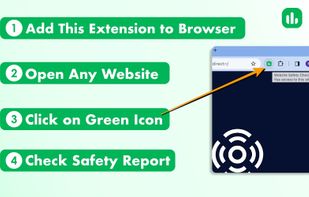
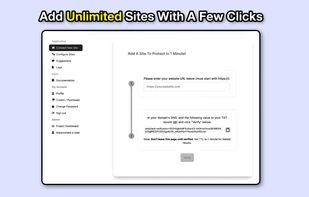
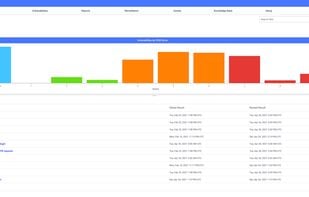
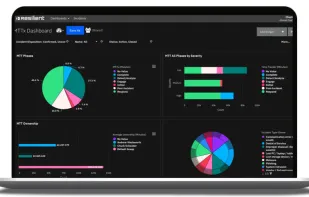
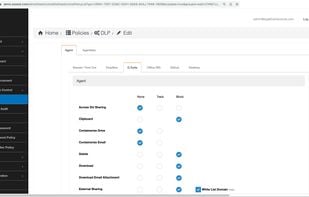
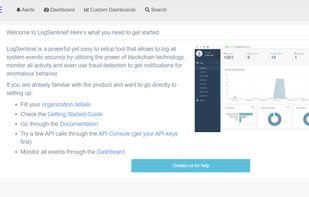
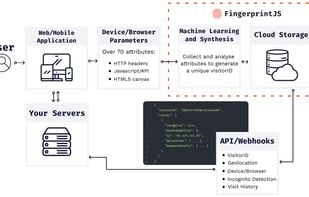
Safe Me is a free cybersecurity app that helps you improve the security of your or any other mobile you want to by providing you with a personalized score, giving a personalized recommendation, and monitoring your mobile for dark web exposure.
- Free • Proprietary
- Android
- iPhone
- Software as a Service (SaaS)