AI powered phishing detection for Gmail. One click to scan suspicious emails for fake domains, urgent language, and social engineering. Get instant risk scores with clear explanations.
- Free • Proprietary
- Google Chrome
- Online
- Gmail
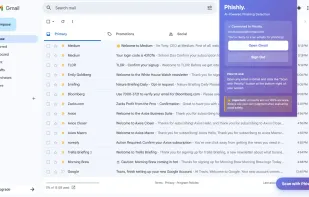
AI powered phishing detection for Gmail. One click to scan suspicious emails for fake domains, urgent language, and social engineering. Get instant risk scores with clear explanations.

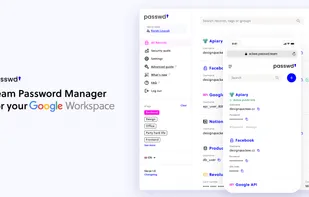
Passwd is your go-to team password manager for Google Workspace. Designed to seamlessly integrate with your everyday apps like Gmail and Google Calendar, Passwd eliminates security worries and organizational chaos.
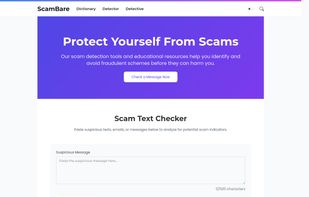
ScamBare empowers you with the resources you need to detect and prevent scams, report and expose online fraud tactics, and stay safe against fraudulent activities.
Do you do client work from coffee shops? Check your bank balance from the airport? Get tired of being stalked by ad networks and trackers as you browse at home?
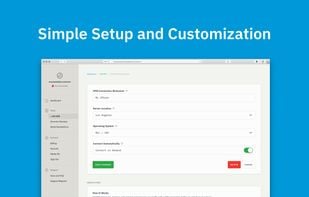
SecureCircle delivers a SaaS-based cybersecurity service that extends Zero Trust security to data on the endpoint. At SecureCircle, we believe frictionless data security drives business value for our customers.
Reduce your reaction time to hackers thanks to Trapster's honeypot which quickly alerts you in case of intrusion on your company's network.
An AI-driven cybersecurity platform that automates vulnerability assessments, real-time threat detection, and reporting. It helps organizations and individuals effortlessly secure their digital assets through automated scans, continuous monitoring, and actionable insights...

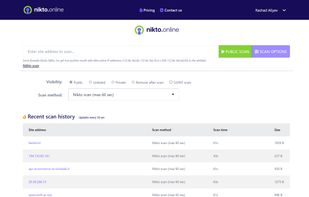
At Nikto Online Scanner, we are dedicated to providing a comprehensive solution for assessing the security of web servers. Our platform offers a powerful tool that conducts extensive tests to identify potential vulnerabilities, misconfigurations, and security risks associated...
This Environment allows people to work on large array of android security related task’s ranging from Malware Analysis, Penetration Testing and Reverse Engineering.

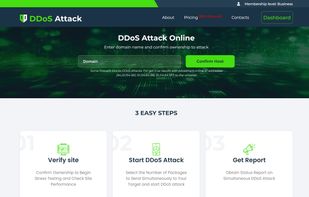
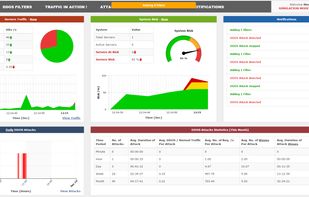
"Online DDoS Attack Simulation portal" is a web-based platform designed to simulate and test Distributed Denial of Service (DDoS) attacks on networks, websites, or online services. DDoS attacks are malicious attempts to overwhelm a target server or network with a...
CyberUpgrade is an advanced ICT security and compliance platform transforming "paper security" into tangible business resilience.
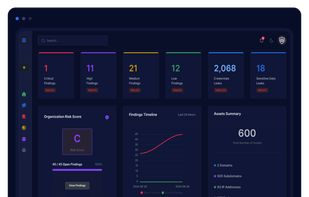
Flawatch is a Continuous Threat Exposure Management (CTEM) solution designed to help organizations automate and streamline security operations by providing dark web monitoring, cyber threat intelligence (CTI), attack surface management, and code leaks discovery.
We are a security awareness training solution built exclusively for schools. Your new affordable K-12-friendly solution
It notifies instantly about unauthorized use of phone camera, microphone, the premium version offer also the data log by apps via internet, whitelists, block.
Anjuna Confidential Computing software makes the public cloud the safest and most secure place to compute--completely isolating existing data and workloads from insiders, bad actors, and malicious code.
Cutting-edge security meets convenience: Authenticator° is the ultimate iOS app designed to make your digital life safer and hassle-free. Now supporting Apple Watch, we safeguard your accounts across Twitter, Reddit, LinkedIn, Instagram, TikTok, Amazon, Facebook, Dropbox...


L7 Defense system is a virtual platform for mitigating sophisticated DDoS attacks automatically and efficiently in Real Time. Enhancing the self-learning intelligence of the immune system with dedicated ML components enables the system to easily mitigate unknown, under the...
Security Bulldog is reshaping the way enterprises handle cybersecurity vulnerabilities. By leveraging an AI-powered intelligence platform, it reduces both the cost and the time necessary for effective remediation, allowing teams to focus on strengthening their defenses rather...
Huntr is a free security tool for auditing compromised credentials. It aggregates data from HaveIBeenPwned, XposedOrNot, and LeakCheck.io into a single search, including a client-side password generator. Built by a student dev for the security community.
Zyphe's privacy-first identity verification solution makes user onboarding more secure and seamless, helping companies keep PII off their servers and stay ahead of privacy and security risks. We use the latest decentralization and Web3 technology for secure identity sharing...
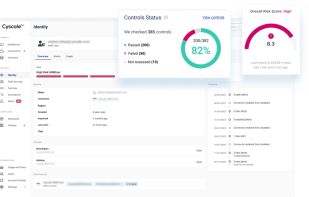
Cyscale is a cloud-native security solution that constantly monitors your cloud environment. Designed to identify potential risks and prioritize remediations, it becomes an invaluable tool for Security Teams, CISOs, and CTOs looking to bolster their security posture.
msX Guard is a global, publicly accessible database of dangerous and unsafe domains, developed by Ixavence Bagart. It helps developers, browsers, and search engines detect and block phishing, malware, and scam websites before users interact with them.
Train, test and track your security awareness in one comprehensive solution. High quality cyber training that impresses your users and meets board requirements. Integrated phishing simulation to test the efficacy of your awareness program.
Ekran System® is a universal insider threat protection platform helping business with employee monitoring, subcontractor control, PAM, and compliance tasks.