Directory/File, DNS and VHost busting tool written in Go - GitHub - OJ/gobuster: Directory/File, DNS and VHost busting tool written in Go
Cost / License
- Free
- Open Source (Apache-2.0)
Platforms
- Linux
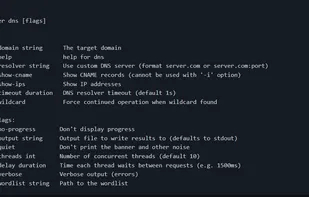
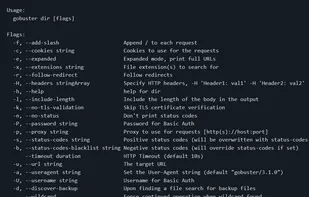
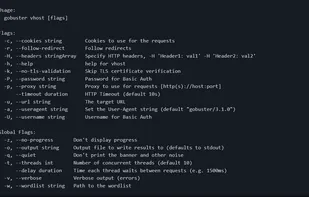
Directory/File, DNS and VHost busting tool written in Go - GitHub - OJ/gobuster: Directory/File, DNS and VHost busting tool written in Go



Matriux is a fully featured security distribution consisting of a bunch of powerful, open source and free tools that can be used for various purposes including, but not limited to, penetration testing, ethical hacking, system and network administration, cyber forensics...


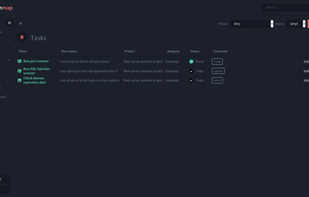
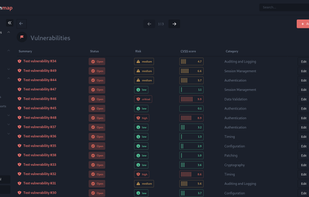
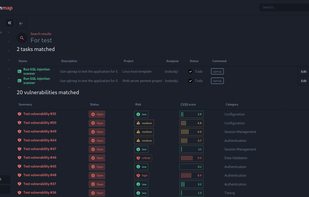
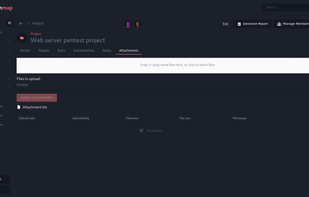
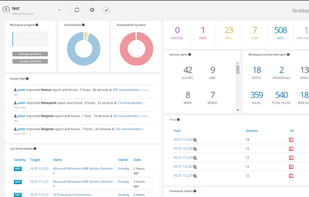
Reconmap is an open-source tool for InfoSec teams to collaborate on pentest and other security projects. They can create projects from templates, keep track of tasks, upload results and get automatic insights that are available on the browser and in customisable HTML and PDF...
Elevate your hacking skills at Parrot CTFs! We provide premier ethical hacking training and labs, catering to beginners and pros. Join our global community and level up your cybersecurity skills with our realistic hacking labs and challenges.

Find security vulnerabilities right from your browser. Experience the next generation security tools without the need to install any additional software.


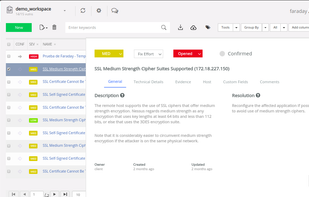
Fully customisable, offensive security reporting tool designed for pentesters, red teamers and other security-related people alike.
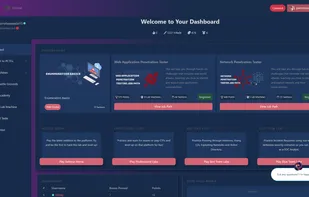
Collaborative Penetration Test and Vulnerability Management Platform that increases transparency, speed and efficiency for your audits & team.
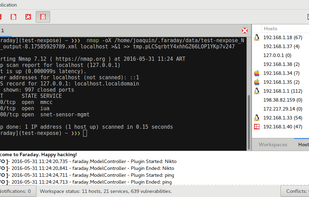
DIRB is a Web Content Scanner. It looks for existing (and/or hidden) Web Objects. It basically works by launching a dictionary based attack against a web server and analyzing the response.
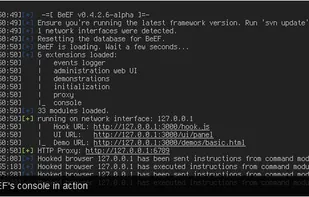
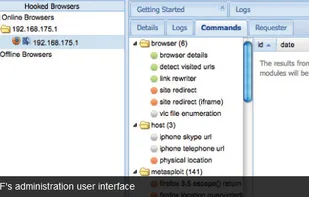
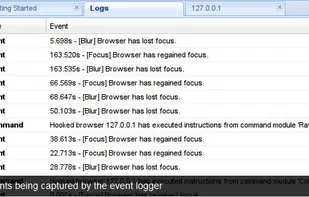
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
Immunity's CANVAS makes available hundreds of exploits, an automated exploitation system, and a comprehensive, reliable exploit development framework to penetration testers and security professionals worldwide.
Websecurify is a powerful web application security testing environment designed from the ground up to provide the best combination of automatic and manual vulnerability testing technologies.
Hack This Site is a free training ground for users to test and expand their hacking skills. Our community is dedicated to facilitating an open learning environment by providing a series of hacking challenges, articles, resources, and discussion of the latest happenings in hacker...


Human-in-the-loop penetration testing enhanced with AI. Identify vulnerabilities faster, reduce risk, and stay audit-ready with actionable reports and real-time visibility.
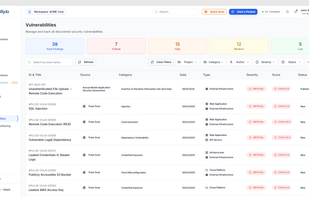
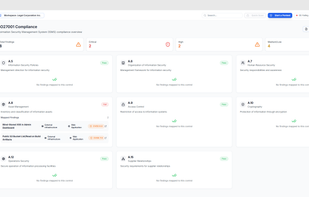
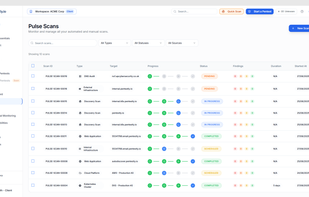
Barrion helps developers and tech teams secure their web applications by automating security checks. It scans websites and web apps for common vulnerabilities, evaluates SSL/TLS and email security (SPF, DKIM, DMARC), and checks security headers and outdated software.
Wireless Air Cut is a WPS wireless, portable and free network audit software for Ms Windows. It is used to check the security of our WPS wireless networks and to detect possible security breaches.
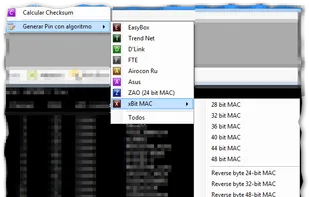
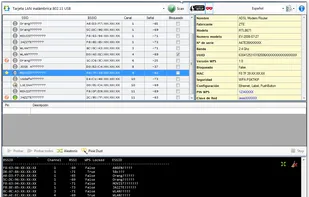
The most advanced, powerful and yet beautiful penetration testing distribution ever created.Lined up with ultimate collection of tools for pro Ethical Hackers and Cyber Security Experts.
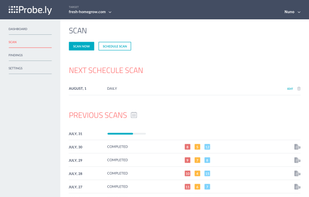
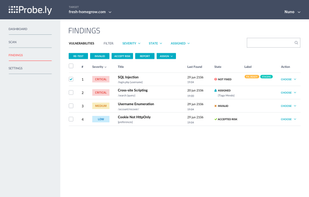
Probely is a top-tier cloud-based DAST Scanner designed for DevOps, empowering Security and Development teams to work together to secure their web applications and APIs.
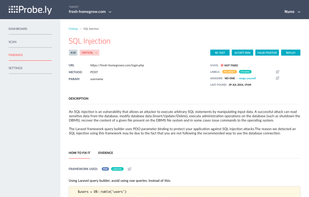
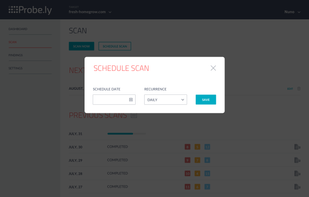
In today's digital landscape, your online presence is constantly at risk. Cybercriminals are becoming increasingly sophisticated, and the stakes have never been higher. Your sensitive information, client data, and even your reputation are on the line.

PENTESTON is a cloud-based Cybersecurity platform that allows you to oversee the complete secure development lifecycle of your application. It functions as a cyber security reporting and workflow management system, providing you with the necessary tools to manage the entire...
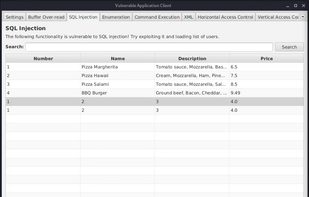
Vulnerable Client-Server Application (VuCSA) is made for learning/presenting how to perform penetration tests of non-http thick clients. It is written in Java (with JavaFX graphical user interface).
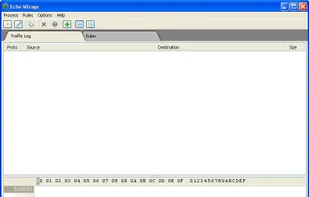
Echo Mirage, a freeware tool that hooks into an application’s process and enables us to monitor the network interactions being done. This process can be done with a running process, or it can run the application on the user’s behalf.
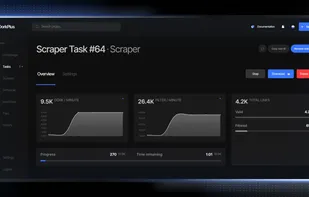
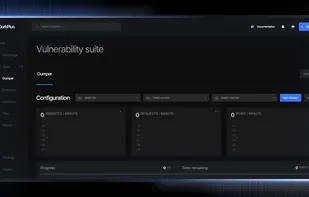
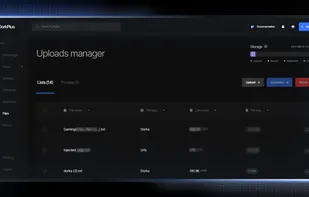
DorkPlus is a all in one solution with more than 10 modules including a Web Scraper (Google, Bing, Ask...), a Vulnerability Scanner (SQL, XSS, ENV..), a Database Dumper, and more unique built-in tools dedicated to pentesting.
Core Impact Pro is the most comprehensive software solution assessing and testing security vulnerabilities throughout your organization. Core Impact Pro tests across a broad spectrum of risk areas including:
Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible.
This open-source project aims to provide a user-friendly tool to learn about keystroke injection attacks and 'BadUSBs'.