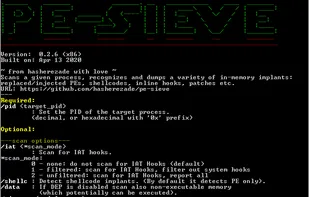
PE-sieve
PE-sieve scans a given process, searching for the modules containing in-memory code modifications. When found, it dumps the modified PE. Detects inline hooks, hollowed processes, Process Doppelgänging etc. Can be used for unpacking malware.
Features
- Portable
- Process Monitoring
PE-sieve News & Activities
Recent activities
PE-sieve information
What is PE-sieve?
PE-sieve is a tool that helps to detect malware running on the system, as well as to collect the potentially malicious material for further analysis. Recognizes and dumps variety of implants within the scanned process: replaced/injected PEs, shellcodes, hooks, and other in-memory patches. Detects inline hooks, Process Hollowing, Process Doppelgänging, Reflective DLL Injection, etc.
PE-sieve is meant to be a light-weight engine dedicated to scan a single process at the time. It can be built as an EXE or as a DLL. The DLL version exposes a simple API and can be easily integrated with other applications.
If instead of scanning a particular process you want to scan your full system with PE-sieve, you can use HollowsHunter. It contains PE-sieve (a DLL version), but offers also some additional features and filters on the top of this base.