The industry's leading privacy-oriented threat intelligence and file reputation solution. Available via AWS cloud, or locally hosted in your environment. Full support available for private network deployments.
Easy Report Alternatives
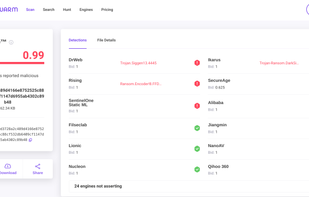
Easy Report is described as 'Helps you identify hosting providers and generate abuse reports for phishing, malware, copyright infringement, and other violations' and is an website in the security & privacy category. There are more than 25 alternatives to Easy Report, not only websites but also apps for a variety of platforms, including Windows, Linux, Mac and Google Chrome apps. The best Easy Report alternative is VirusTotal. It's not free, so if you're looking for a free alternative, you could try VirusTotal or Avast Free Antivirus. Other great sites and apps similar to Easy Report are urlscan.io, MetaDefender, Cuckoo Sandbox and ANY.RUN.
Alternatives list
A lightweight security threat scanner intended to make malware detection more accessible and efficient.
 +1
+1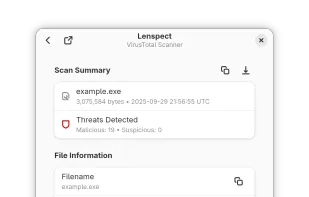
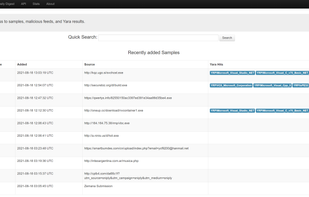
The MalShare Project is a community driven public malware repository that works to provide free access to malware samples and tooling to the infomation security community.
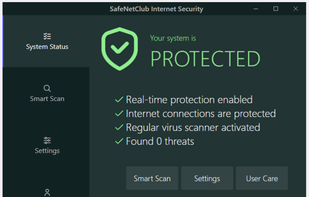
SafeNetClub is an antivirus software that protects your PC against cyber threats. The application is connected with a realtime virus database to scan the system, all incoming traffic and files to avoid damage of the computer, spy attacks and data theft.
A malware-analysis tool that identify the exact position and details of malicious content in binary files using external Anti-Virus scanners. Supports all AV scanners.

PolySwarm is a more effective way to detect, analyze and respond to the latest malware threats. Polyswarm is a launchpad for innovative threat detection methods. Antivirus companies and specialized engines compete with each other to detect threats.