Find a geolocation of an IP address including latitude, longitude, city, region and country.
- Free • Proprietary
- Online
Find a geolocation of an IP address including latitude, longitude, city, region and country.
You no longer need to call IT to connect your new iPhone, iPad, or iPod touch with your corporate infrastructure. Using Tangoe Mobile, you can self-authenticate, authorize, and configure your iOS device without help from IT.

The Snare Server, from InterSect Alliance, is a proprietary Log Monitoring solution that builds on the open source Snare agents to provide a central audit event collection, analysis, reporting and archival system.
GRC Internet Security Port Scanner. Tests for open ports on your external IP address.
Syspeace automatically blocks brute force attacks primarily for Windows Servers with good information in the admin mils telling you DNS names, country of origin and username used for the attack.
LANwriter is a unique intranet software application for centralized, secure and audited publishing of data to CDs, DVDs, Pen Drives and FTP servers via a single computer on the network that acts as a device server and data gatekeeper and is a powerful data leak prevention tool.
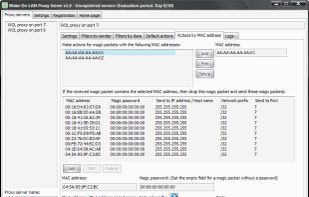
Wake-On-LAN Proxy Server is a network tool that helps network administrators to organize the reception and transmission of magic packets (wakeup signals, which are sent through programs that support the Wake-on-LAN technology) on the network.
Pypacker is a fast and simple packet creation and parsing library for Python. It lets you create packets manually by defining every aspect of all header data and dissect packets by parsing captured packet bytes.
Use the MikroTik smartphone app to configure your router in the field, or to apply the most basic initial settings for your MikroTik home access point.
Secure infrastructure, applications and data across hybrid and multi-cloud environments.
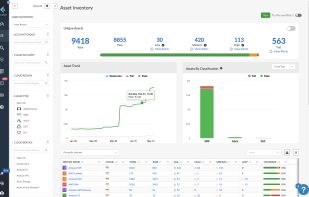
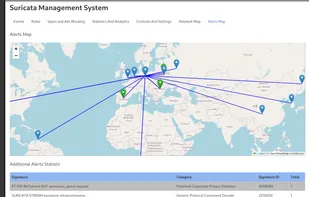
Suri Oculus is a high-performance platform for Suricata management, real-time network event processing (via Redis), lightweight visualization, AI-driven anomaly detection, and automated domain-intelligence workflows.
trafMon, an open source network traffic performance monitoring and diagnostics tool.

What is Nethor? A "Device Matrix" layout displaying properties for a node. In addition, the context menu for another node, the search dialog and the Traceroute tool are shown. Above the matrix is the Timeline.
Vyopta is your all-in-one monitoring and analytics solution for enterprise UC networks. Drive adoption and head off problems with Acano, Cisco, WebEx, Polycom, Pexip and more from one user-friendly dashboard.
Knocknoc removes the attack surface of existing infrastructure by orchestrating network-level access controls, whilst integrating seamlessly with identity platforms. By keeping ports closed and services invisible until centralised authentication has occurred, Knocknoc removes...
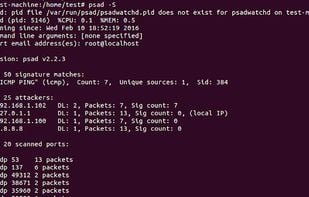
psad is a collection of three lightweight system daemons (two main daemons and one helper daemon) that run on Linux machines and analyze iptables log messages to detect port scans and other suspicious traffic.
FerrumGate is an Open source Zero Trust Access (ZTA) project, that uses advanced identity and access management technologies to ensure secure access to your network and applications. With multi-factor authentication, continuous monitoring, and granular access controls.
The syslog-ng Store Box™ (SSB) is a high-performance, high-reliability log management appliance that builds on the strengths of syslog-ng Premium Edition.
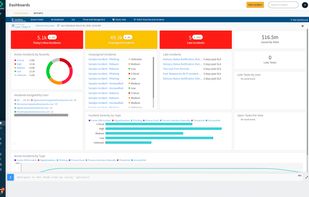
Rapid7 is engineering better security to help companies reduce risk of breach, detect and respond to attacks, and build effective cybersecurity programs.
Complete, real-time change auditing, in-depth forensics and comprehensive reporting on all key configuration, user and administrator changes for your Windows environment and beyond.
ExtremeAI Security utilizes the power of machine learning and artificial intelligence to identify and remediate advanced threats. Extreme revolutionizes the experience for security analysts by providing proactive, automated, remediated capabilities.
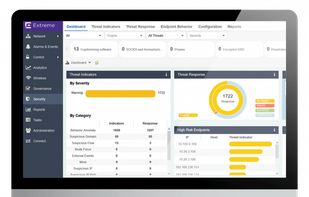
The industry’s most comprehensive SOAR platform.
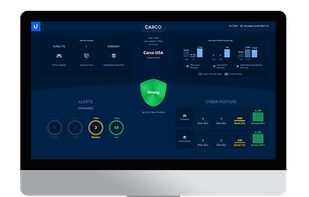
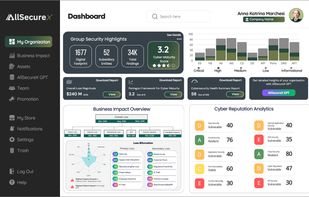
AllSecureX helps CISOs and boards translate complex cyber threats into real-time financial impact insights. By combining AI, automation, and quantum-safe modeling, AllSecureX enables smarter, faster, and board-ready security decisions.
Upstream Security is the first cloud-based centralized cybersecurity and analytics platform that protects the technologies and applications of connected and autonomous vehicles fleet.