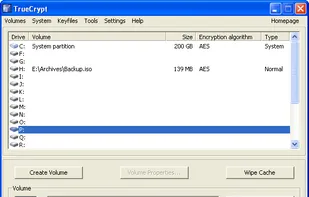
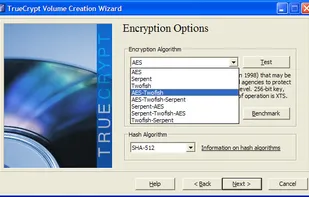
[TrueCrypt is not exactly "Open Source", but the source is available. See the reviews to get more information.]
Cost / License
- Free
- Proprietary
Application type
Alerts
- Discontinued
Platforms
- Mac
- Windows
- Linux


Krypta is described as 'Discontinued' and is an app in the security & privacy category. There are more than 10 alternatives to Krypta for a variety of platforms, including Windows, Linux, Mac, OpenPGP and Android apps. The best Krypta alternative is TrueCrypt, which is free. Other great apps like Krypta are GnuPG, Kleopatra, Axcrypt and Windows BitLocker.
[TrueCrypt is not exactly "Open Source", but the source is available. See the reviews to get more information.]




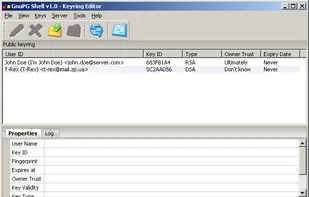
GnuPG allows to encrypt and sign your data and communication, features a versatile key management system as well as access modules for all kinds of public key directories. GnuPG, also known as GPG, is a command line tool with features for easy integration with other applications.
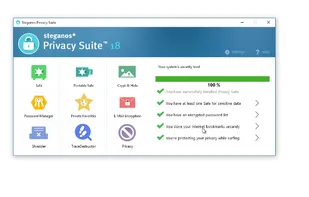
Offers robust file encryption with AES-256 for premium and AES-128 for free users, integrated password manager, intuitive interface, support for cloud storage, multilingual options, offline security, group management tools, and secure file deletion features.




BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
Platform-independent password-based authenticated encryption of files & folders.
LibreCrypt (formerly DoxBox) is an open-source disk encryption for Windows and the successor of FreeOTFE
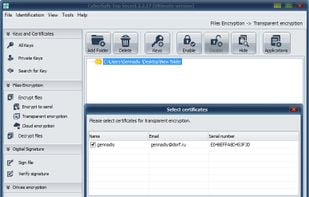
CyberSafe Top Secret is an information security program that uses modern encryption algorithms (RSA, AES, BlowFish, etc.).
The Gostcrypt project has been launched at the end of 2013 as fork of the (late) Truecrypt project.
Xecrets Ez is an easy to use personal desktop application available for Windows, Mac and Linux. It is 100% compatible with AxCrypt, but is less complex without the bells and whistles.
Now this is what I call real security!... You may use any one of nineteen, industrial and military strength, encryption ciphers to secure your most precious private information.