Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.
I2P+ is described as 'Enhanced version of the Java I2P anonymizing network platform that aims to deliver a superior user experience and improved network performance while retaining full compatibility with upstream I2P' and is a anonymizing network in the security & privacy category. There are nine alternatives to I2P+ for a variety of platforms, including Mac, Windows, Linux, BSD and Self-Hosted apps. The best I2P+ alternative is Tor, which is both free and Open Source. Other great apps like I2P+ are Snowflake Tor, IPFS, ZeroNet and GNUnet.
Tor is free software and an open network that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security.


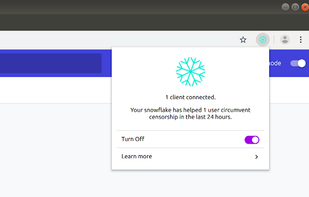
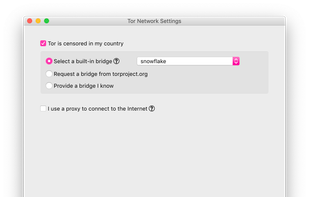
Snowflake is a system to defeat internet censorship. People who are censored can use Snowflake to access the internet. Their connection goes through Snowflake proxies, which are run by volunteers.
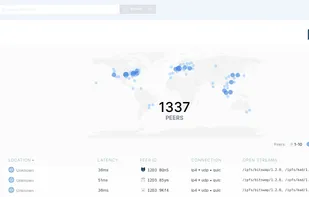
IPFS is a global, versioned, peer-to-peer filesystem. It combines ideas from Git, BitTorrent, Kademlia, SFS, and the web. It is like a single bittorrent swarm, exchanging git objects. IPFS provides an interface as simple as the HTTP web, but with permanence built in.

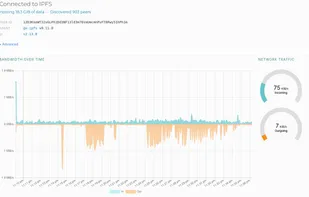
ZeroNet uses cryptography (Bitcoin library) and BitTorrent DHT (centralized trackers) to build a distributed censorship-resistant network.
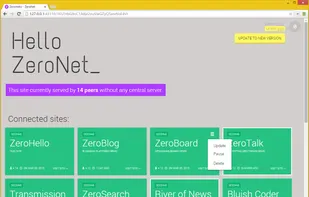
GNUnet is a framework for secure peer-to-peer networking that does not use any centralized or otherwise trusted services. A first service implemented on top of the networking layer allows anonymous censorship-resistant file-sharing.
I2P (Invisible Internet Protocol) is a universal anonymous network layer. All communications over I2P are anonymous and end-to-end encrypted, participants don't reveal their real IP addresses.
Imagine a decentralized network maintained by other users just like you. Here all your personal files are encrypted and only you hold the key to unlock them. Completely anonymous and secure.
In early 2005, a few people fed up with the way the Internet was heading, began in earnest to create a large wide area network that was secure and lived in its own space. On this new network anyone would be free to do as they saw fit - roam about, host services, or just be...
I2P Browser is an enhanced private browser for the decentralized, private I2P network and an easy to use client for I2P applications like peer-to-peer file-sharing, messaging, and e-mail.