Batch File Encryptor
2 likes
Encrypt and decrypt whole files or their parts using AES, 3-DES, RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection.
Cost / License
- Paid
- Proprietary
Platforms
- Windows
Features
- Portable
- Batch conversion
- Batch processing
Batch File Encryptor News & Activities
Highlights All activities
Recent activities
 TheEmperorArt added Batch File Encryptor as alternative to FileCryptor
TheEmperorArt added Batch File Encryptor as alternative to FileCryptor AScomp added Batch File Encryptor as alternative to Guardian Of Data
AScomp added Batch File Encryptor as alternative to Guardian Of Data
Batch File Encryptor information
No comments or reviews, maybe you want to be first?
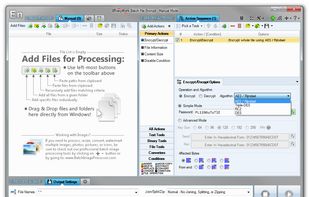
What is Batch File Encryptor?
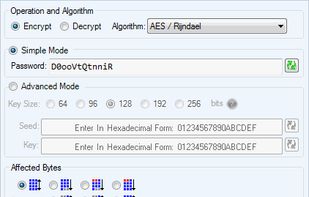
Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms.
- You can encrypt files with a single password or specify cryptographic keys (vectors) instead.
- You can change key bit length for better protection.
- You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
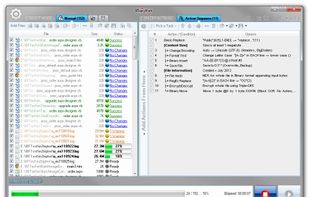
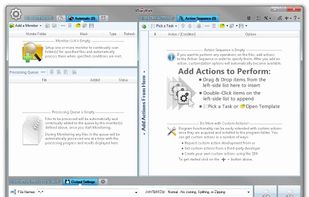
- Process 1000s of files using multiple CPU cores in manual, automatic/continuous, triggered/scheduled, or console modes, or directly from Windows Explorer right-click menu.
- Save files to output directory specified using either absolute or relative path, with original or new name defined by a mask.
- Select files for processing based on their name, dates, size, and contents using advanced file search supporting RegEx and advanced wildcards.
- Optionally merge together, split all, or zip processed files.
- Perform different operations on different files with conditional processing and process branching.
- Detailed processing logs are available in both user interface and log files.
- Run multiple program instances simultaneously.