Website repository that checks what sites your email address was used on were compromised.
LeakCheck is described as 'Offers a search engine with a database of more than 7 billion leaked records. Users can search for leaked information using email addresses, usernames, phone numbers, keywords, and domain names. Our goal is to safeguard the data of people and companies' and is a Data Breach tool in the online services category. There are more than 25 alternatives to LeakCheck, not only websites but also apps for a variety of platforms, including Windows, Linux, Self-Hosted and Mac apps. The best LeakCheck alternative is Have I Been Pwned, which is free. Other great sites and apps similar to LeakCheck are Data Breach Observatory, Mozilla Monitor, Intelligence X and DeHashed.
Website repository that checks what sites your email address was used on were compromised.

Automated system scans dark web sources to deliver real-time breach alerts when sensitive data or credentials are discovered, empowering businesses to investigate, respond promptly, prevent further exposure, and maintain security by identifying compromised accounts and files.

Mozilla Monitor arms you with tools to keep your personal information safe. Find out what hackers already know about you and learn how to stay a step ahead of them.
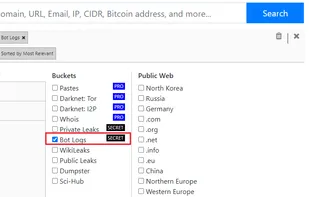
Intelligence X is a search engine and data archive. Search Tor, I2P, data leaks and the public web by email, domain, IP, CIDR, Bitcoin address and more.
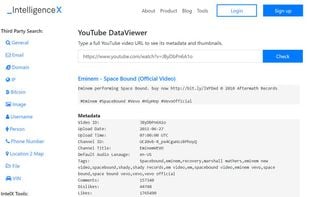
DeHashed is the largest & fastest data breach search engine. You can search for IP address, email, username, name, phone, VIN, address, and more! We have true wild card, dork usage, and we offer a real search engine experience! It's also free!.
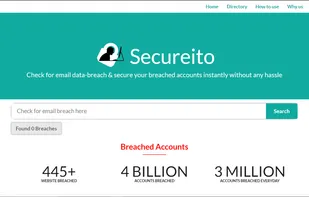
Check for Email data-hack & secure your hacked accounts instantly in one click. It generally takes a lot of time & manual efforts in securing all your accounts. With secureito, Users can secure their hacked accounts in a second.
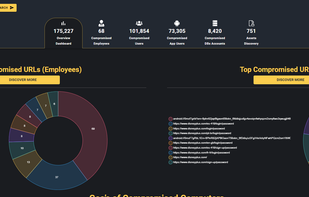
With expertise developed at the cybercrime intelligence division at the prestigious 8200 cyber unit at the IDF, Hudson Rock’s powerful cybercrime threat intelligence feed provides invaluable data for infrastructure protection, end-user protection, and supply chain risk...
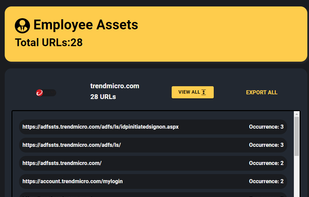
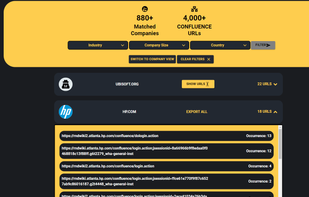
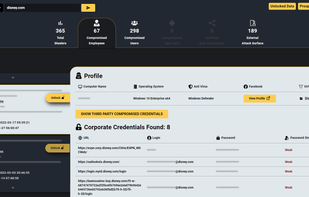
The industry leading database lookup. We pride ourselves in being faster than all of our competitors, wile maintaining a very large selection of private databases.

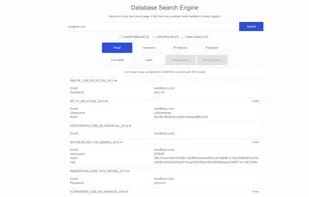

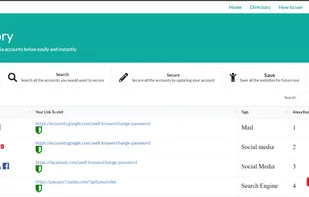
Protect your account, discover its leaks, avoid using insecure passwords. Breach search engine powered by LeakCheck.net. Check if your password was compromise before it's too late. More results than HIBP.
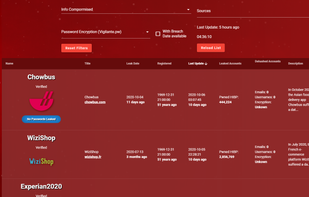
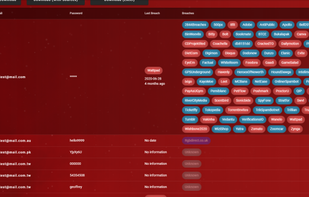
OSINT Investigation tool for advanced searches using Phone Numbers, Emails, and more. Secure, fast, and precise analysis for your Investigations.
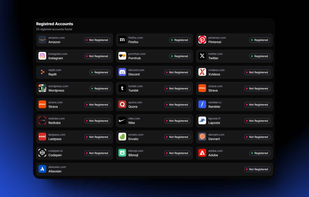
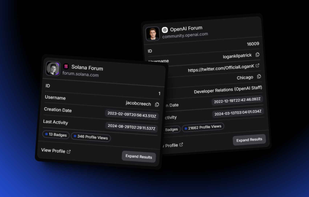
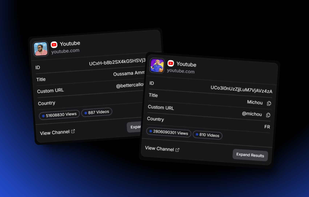
LeakRadar.io monitors and detects data leaks related to your domains, email addresses, and keywords. It offers various plans suited for personal use, small companies, and large enterprises, with real-time alerts, an API, and advanced breach prevention tools.
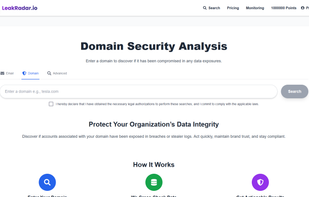
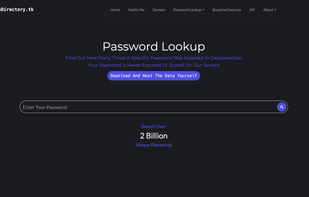
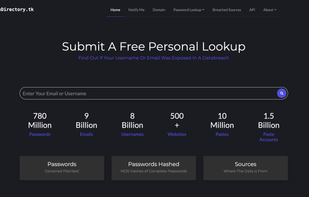
BreachDirectory allows you to search through all public data breaches to make sure your emails, usernames, passwords, and domains haven't been compromised.