Frida
Frida is a free open-source dynamic instrumentation toolkit for developers, reverse engineers, and security researchers created and supported by NowSecure researchers.
Cost / License
- Free
- Proprietary
Platforms
- Self-Hosted
- Python
- Node.JS
- npm
Features
Frida News & Activities
Recent activities
Frida information
What is Frida?
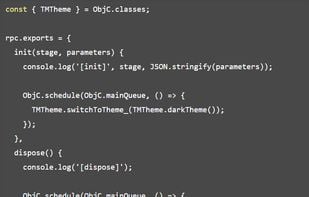
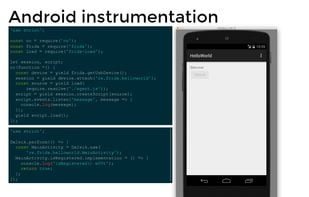
It’s Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, watchOS, tvOS, Android, FreeBSD, and QNX. Frida also provides you with some simple tools built on top of the Frida API. These can be used as-is, tweaked to your needs, or serve as examples of how to use the API.
Inject your own scripts into black box processes. Hook any function, spy on crypto APIs or trace private application code, no source code needed. Edit, hit save, and instantly see the results. All without compilation steps or program restarts.
The Frida core is written in C and gets injected along with JavaScript into the target processes, where your JS gets executed with full access to memory, hooking functions and calling native functions. It enables a bi-directional communication channel that is used between your app and the JS running. Using Python and JS allows for quick development with a risk-free API. Frida can help catch errors in JS and provide an exception rather than crashing, and can use Python, C, Node.js, Swift, .NET, Qml, and more. Frida can run in 3 modes: Injected, the most common approach, Embedded and Preloaded through Frida’s Gadget, a shared library meant to be loaded by programs.