

BeyondTrust
BeyondTrust offers the industry’s broadest set of privileged access management capabilities to defend against cyber attacks.
Cost / License
- Subscription
- Proprietary
Application type
Platforms
- Software as a Service (SaaS)
Features
- User Session Recording
- Remote Support
BeyondTrust News & Activities
Recent News
Recent activities
- water-vole updated BeyondTrust
 POX added BeyondTrust as alternative to Rabbit Remote Control and Field Monitor
POX added BeyondTrust as alternative to Rabbit Remote Control and Field Monitor- POX added BeyondTrust as alternative to Bananas Screen Sharing
BeyondTrust information
Featured in Lists
An updated list of my most-used software as a Systems Administrator
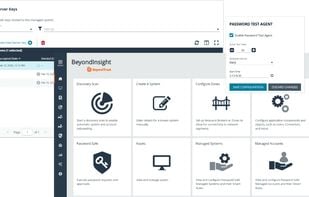
What is BeyondTrust?
Privileged Access Management with a Fast Time-to-Value
In a world of stolen identities, phished passwords, and deep fakes, you can't just trust users and systems. You need to know identities and access pathways are secure. The BeyondTrust platform enables identity and access security that is monitored, managed, secured, and just-in-time.
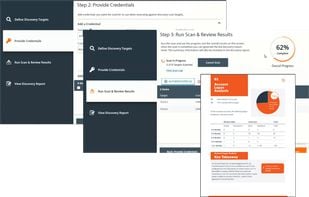
Privileged Password Management Discover, manage, audit, and monitor privileged accounts and credentials.
Endpoint Privilege Management Enforce least privilege across Windows, Mac, Linux, and Unix endpoints.
Secure Remote Access Centrally manage remote access for service desks, vendors, and operators.
Cloud Security Management Automate the management of identities and assets across your multicloud footprint.


Comments and Reviews
I'm using it in a large business, also with unattended access etc. Has many features.
An alternative to Bombar is RHUB remote access. Like Bomgar, RHUB is also an appliance that is deployed on-premise, but unlike them they (RHUB) also have web conferencing. It works on multiple platforms, and is fast, easy to install, and highly secure.