

SSL Enforcer
2 likes
SSL Enforcer - Force SSL/TLS encryption for any browser or app. Block all unsecure connections. Windows 7, 8, 8.1; 10 Mac OS X 10.9 - 10.14
Cost / License
- Free
- Proprietary
Platforms
- Mac
- Windows
Features
No features, maybe you want to suggest one?
SSL Enforcer News & Activities
Highlights All activities
Recent activities
No activities found.
SSL Enforcer information
Featured in Lists
Master List of all Apps and Software I use for both work and personal life.
List by Jimmy Briggs with 421 apps, updated
What is SSL Enforcer?
SSL Enforcer - Force SSL/TLS encryption for any browser or app. Block all unsecure connections. Windows 7, 8, 8.1; 10 Mac OS X 10.9 - 10.14
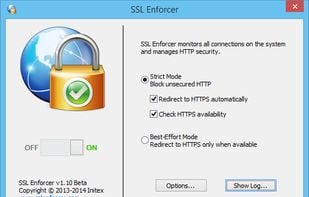
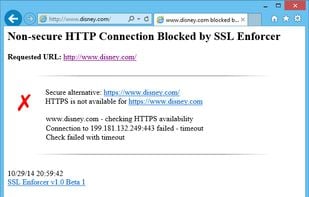
Today any network activity involves a number of requests to the web. It is hard to make sure that all connections go through secure channels (SSL/TLS). This can compromise your security. SSL Enforcer can automatically block all unsecure HTTP connections, check for secure alternatives (HTTPS) and reroute the connections accordingly.
Key Features:
- Works for all apps including browsers, plug-ins and any other Internet clients.
- No data leaks. Blocks unsecure connections on the system level starting from the very first request.
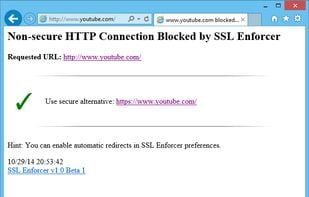
- Switches to secure connections (HTTPS) automatically if available.
- Flexible rules based on application name, target host and port.
- Does not use a tunnel or proxy server. Your traffic goes directly to the target with maximum speed.




Comments and Reviews
I like that this isn't a browser extension. Latest release 2019.