Oversecured
Oversecured is an online service designed to search security vulnerabilities in mobile apps. It's adapted to Android security and privacy. It can detect a lot of different attack vectors and privacy issues (starting from known arbitrary code executions, theft/overwrite of...
Cost / License
- Pay once or Subscription
- Proprietary
Application type
Platforms
- Android
- Software as a Service (SaaS)
Features
- Android Security
- Static Code Analysis
Oversecured News & Activities
Recent activities
Oversecured information
What is Oversecured?
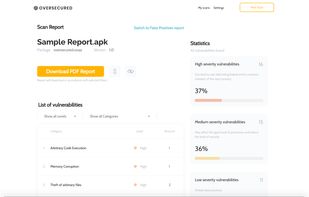
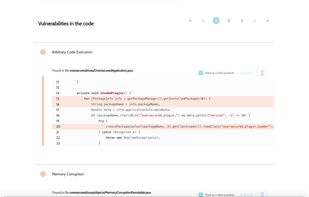
Oversecured is an online service designed to search security vulnerabilities in mobile apps. It's adapted to Android security and privacy. It can detect a lot of different attack vectors and privacy issues (starting from known arbitrary code executions, theft/overwrite of arbitrary files, and ending with ability to theft user pictures, fake SMS messages, leak Android app logs, the full list is available here https://oversecured.com/vulnerabilities), the kernel tracks unsafe and potentially dangerous data from the browser, third-party apps, a network shared with an attacher, Bluetooth and NFC connections, SMS messages, local public storage, etc. We accept APK files (Android apps), decompile them to Java sources, and perform analysis against them. An Oversecured's user will receive a report showing a trace of data in the app's sources, displaying where the dangerous data is coming from, sources that will process that data, and the place where's the vulnerability happens.