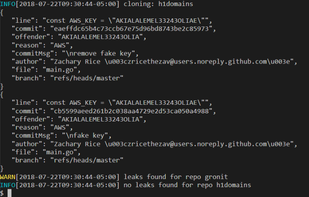
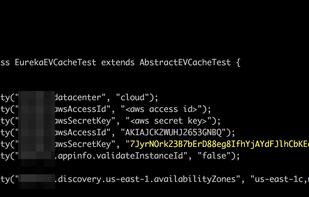
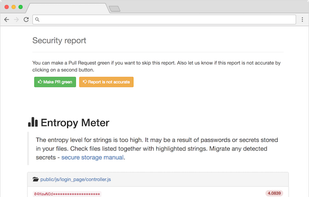
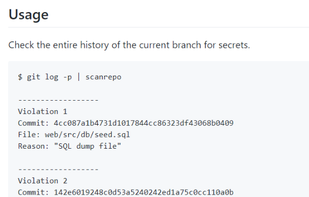
GitGuardian is a global cybersecurity startup focusing on code security solutions for the DevOps generation. A leader in the market of secrets detection and remediation, its solutions are already used by hundred thousands developers in all industries.
Cost / License
- Free Personal
- Proprietary
Platforms
- Self-Hosted
- Software as a Service (SaaS)